- Home
- Knowledge hub
How to comply with IEC 62443 in manufacturing?
2 min. read
Shelly Boom
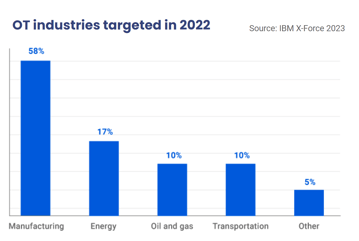 Cybersecurity in manufacturing
Cybersecurity in manufacturingThe cybersecurity landscape has seen a couple of trends in the last decade. From total number of attacks to number of ransomware attacks and number of successful attacks: all are increasing. The costs and damage of cyber attacks also continue to rise.
But why is manufacturing a prime target for hackers? There are 3 reasons for it:
Both government and market are now taking actions to increase cybersecurity in manufacturing.
The government’s response has been to strengthen cybersecurity across sectors through regulations like NIS2, DORA, the Cyber Resilience Act, GDPR, and more. These regulations aim to improve organizational security, though they're rather basic and limited in scope.
On the other hand, you have the market response. The market is starting to expect (and even demand) that you as a supplier have compliance with certain regulations and industry standards. Think of IEC 62443 for the manufacturing industry.
At IXON, we see IEC 62443 as the gold standard for manufacturing. There are 5 reasons for it:
Want to have more explanation on why IEC 62443 is the right standard? Download our Security kit and read the Practical Guide to IEC 62443 on how to certify machines in compliance with the standard.
The question now is how you can secure your machines. First of all, a secure machine is not just adhering to the IEC standard, and that's it. It's a big part of it, but it's part of a whole. There’s also the organization and the technology you use.
When you look at the IEC 62443 standard, there are 7 requirements. We chose to divided them into 5 themes: Authentication, Auditing, Vulnerability protection, Restricted data flow and Availability. For each theme, we’ve identified 5 recommendations as “low hanging fruits” that come directly from the IEC. If your machine or system adheres to these 25 recommendations, you have done all of the quick wins of the IEC.
Learn everything about these 25 recommendations by watching our webinar replay "How to comply with security requirements" which is part of our Security kit.
IXON made some security documents and tools available to get started yourself. You can download them for free.
The IXON Security kit includes:
